Nationwide Web Services.
Same Day Updates.
Nationwide Web Services.
Same Day Updates.
Nationwide Web Services.
Same Day Updates.
Others Over Promise.
We Over Deliver.
Others Over Promise..
We Over deliver.
Others Over Promise.
We Over Deliver.
Everything You Need.
More Than You Expect.
Everything You Need.
More Than You Expect.
Everything You Need.
More Than You Expect.
Recession? Job cuts? Let us manage your online content: 703-407-4363
LET US BUILD YOUR ONLINE PRESENCE
Web Design
Xpheria is a full-service design firm, providing websites from very basic to very sophisticated. Our online services encompass layout, writing, artwork, photography, video and audio, plus ongoing support.
Writing
With decades of solid marketing success in corporate and non-profit environments, Nathan and Linda Muller have written and illustrated 29 Internet-related books published by McGraw-Hill and others.
Marketing
As more people go online to make purchase decisions, your website must be positioned so it is easy to find. Once people find you, the content about your offerings should encourage them to contact you.
Technical Support
We provide host account and email setup, domain management, database development, website maintenance, problem resolution, security, and backups. You decide the level of service you want.
Single-Source. Custom Solutions. Responsive Support.
TECHNICAL SERVICES
VALUE ADDED SERVICES
Loss Prevention
Xpheria offers multiple levels of backup to prevent the catastrophic loss of your website. Backups are conducted daily and stored at the host server, a mirrored local host, and our own dark cloud.
Read MorePerformance Optimization
Xpheria understands how the user experience can potentially affect the success of your business. We design websites that are fast and reliable on any device - desktop, notebook, tablet and smartphone.
Read MoreWHAT OUR CLIENTS ARE SAYING...
Linda Muller introduced me to the web back in 1995 and ran the Buchanan website in two presidential campaigns, and now the official website which discusses the important issues before our Nation. With gratitude for all she has done for over two decades...
Patrick J. Buchanan, Author & Commentator
You've got to be the hardest working people in the web biz...
Leah Durant, Vaccine Attorney
Xpheria did a spectacular job on my website - it matches my business perfectly.
After only two weeks, my website was at the top of Google search results.
Any changes I need are done the same day.
I could not be happier with my experience!
Dale Phillips, Acme Ammo
I cannot tell you how much I, and our board of directors, appreciate the work you do on our site. We look so impressive, fresh and fantastic with your design work. I just wanted to add some extra thanks as we are so lucky to have you on our team!
Linda Devlin, Allegheny National Forest Visitors Bureau
DECISION-MAKING INFORMATION
The amount of malicious activity on the Internet is growing despite the best efforts of security experts to foil it. When it comes to WordPress sites, attacks are launched across a [...]
According to Cisco, companies today continue to be targeted with a variety of techniques that range from phishing and ransomware to supply chain and social engineering attacks. And [...]
Available since 2007, CAPTCHA and its variants are offered by Google as a free service to help protect websites from spam and abuse. The system distinguishes whether a site visitor [...]
The U.S. government continually pressures tech firms against using end-to-end encryption to keep user communications private and away from the prying eyes of law enforcement. The [...]
Ransomware is a type of malware that is used by cyber criminals to infect computers and encrypt files until a ransom is paid. After the initial infection, ransomware attempts to [...]
When developing a website, there are simple ways to break up content to make your home page more interesting. This will encourage visitors to stay longer and help you achieve your [...]
Outsourcing professional and technical services is viewed as an effective way for businesses to procure the expertise they need on a pay-as-you-go basis without the complexity and [...]
By now you’ve probably heard about the “cloud” and wondered why it’s such a big deal… More companies are moving their business processes to the Cloud, [...]
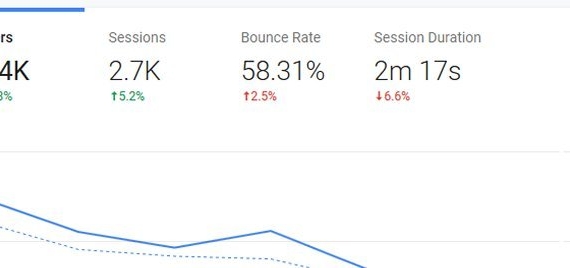
When examining a Google Analytics report of your website’s performance, one metric that may stand out is the bounce rate. This refers to the percentage of visitors who leave your [...]
According to research by Symantec, an alarming 85% of all emails are identified as spam or carry malicious content. That means nearly nine out of 10 emails lack legitimacy, posing [...]
There are dozens of platforms available for building websites, but none is more popular than WordPress. Since its debut in 2003, WordPress has become the easiest and most robust [...]
You’ve interviewed several firms to develop your website. You’ve picked the one that could best meet all of your business needs now and in the future. You’ve signed the [...]
The Cybersecurity and Infrastructure Security Agency (CISA) has announced that throughout October it will focus on ways to “Secure Our World” by educating the public on how to [...]
In the brick-and-mortar world, windows entice shoppers into the store. Online, your website is the “window.” Is it visually exciting? Does it encourage shoppers to explore your [...]
Your website is among hundreds of millions of websites worldwide, so you’re probably wondering why anyone would bother breaking into yours. Sure, you’ve invested time, [...]